Russian hackers allegedly stole over $400 million via crypto-ransomware in 2021. Based on a new report published by blockchain analytics firm Chainalysis on February 14, nearly 74%, or more than $400 million, of ransomware revenue in the past year were channeled into high-risk wallet addresses. These addresses are believed to have been based in Russia.
The report analyzed ransomware hacks in the whole of 2021 and determined their affiliation to Russia via three major characteristics:
- Ransomware programmed only against the victims of non-former-Soviet nations.
- Traces of Russia-based cybercriminal organization known as Evil Corp being behind a particular breach, the group has claimed that it has ties to the Russian government.
- Ransomware strains that share announcements and documents in the Russian language.
Apart from the selection criteria, it seems that web traffic data confirms the huge majority of extorted funds get laundered via Russia. An additional 13% of the funds sent from ransomware addresses to services went to the users who might have been in Russia, more than any other region.
These ransomware strains normally infect a user’s computer through a program exploit, or when downloading unknown files. Then, they encrypt the victim’s file and demand payment via Monero or Bitcoin to a wallet address to make the files highly accessible.
Buy Bitcoin NowOne famous case happened in the past year when Russia-based hacking entity Darkside, through exploiting one leaked password, infected the computer systems of Colonial Pipeline. Eventually, the pipeline’s operators were compelled to pay more than $4 million in crypto ransom. But, $2.3 million of that amount was recovered. But the pipeline had to pay the ransom to regain access to their encrypted files. The ordeal caused a brief fuel crisis.
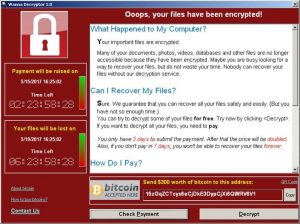
Russian ransomware encryption hack | Source: Reuters









